Java_opts Environment Variable
With this file (which is run by the catalina.bat and catalina.sh scripts), you can change the following Tomcat environment settings with the JAVAOPTS variable: You can set the minimum and maximum memory heap size with the JVM -Xms and -Xmx parameters. JAVAOPTS is a system variable that stores various settings/configurations for your local Java Virtual Machine. By having JAVAOPTS set as a system variable all applications running on top of the JVM will take their settings from this parameter. To setup a system variable you have to complete the steps listed above from 1 to 4.
-->Azure App Service lets Java developers to quickly build, deploy, and scale their Java SE, Tomcat, and JBoss EAP web applications on a fully managed service. Deploy applications with Maven plugins, from the command line, or in editors like IntelliJ, Eclipse, or Visual Studio Code.
This guide provides key concepts and instructions for Java developers using App Service. If you've never used Azure App Service, you should read through the Java quickstart first. General questions about using App Service that aren't specific to Java development are answered in the App Service FAQ.
Deploying your app
You can use Azure Web App Plugin for Maven to deploy your .war or .jar files. Deployment with popular IDEs is also supported with the Azure Toolkit for IntelliJ or Azure Toolkit for Eclipse.
Otherwise, your deployment method will depend on your archive type:
Java SE
Java_opts Environment Variable Windows
To deploy .jar files to Java SE, use the /api/zipdeploy/ endpoint of the Kudu site. For more information on this API, please see this documentation.
Tomcat
To deploy .war files to Tomcat, use the /api/wardeploy/ endpoint to POST your archive file. For more information on this API, please see this documentation.
JBoss EAP
To deploy .war files to JBoss, use the /api/wardeploy/ endpoint to POST your archive file. For more information on this API, please see this documentation.
To deploy .ear files, use FTP.
Do not deploy your .war or .jar using FTP. The FTP tool is designed to upload startup scripts, dependencies, or other runtime files. It is not the optimal choice for deploying web apps.
Logging and debugging apps
Performance reports, traffic visualizations, and health checkups are available for each app through the Azure portal. For more information, see Azure App Service diagnostics overview.
Stream diagnostic logs
To access the console logs generated from inside your application code in App Service, turn on diagnostics logging by running the following command in the Cloud Shell:
Possible values for --level are: Error, Warning, Info, and Verbose. Each subsequent level includes the previous level. For example: Error includes only error messages, and Verbose includes all messages.
Once diagnostic logging is turned on, run the following command to see the log stream:
If you don't see console logs immediately, check again in 30 seconds.
Note
You can also inspect the log files from the browser at https://<app-name>.scm.azurewebsites.net/api/logs/docker.
To stop log streaming at any time, type Ctrl+C.
You can access the console logs generated from inside the container.
First, turn on container logging by running the following command:
Replace <app-name> and <resource-group-name> with the names appropriate for your web app.
Once container logging is turned on, run the following command to see the log stream:
If you don't see console logs immediately, check again in 30 seconds.
To stop log streaming at any time, type Ctrl+C.
You can also inspect the log files in a browser at https://<app-name>.scm.azurewebsites.net/api/logs/docker.
For more information, see Stream logs in Cloud Shell.
SSH console access
To make open a direct SSH session with your container, your app should be running.
Paste the following URL into your browser and replace <app-name> with your app name:
If you're not yet authenticated, you're required to authenticate with your Azure subscription to connect. Once authenticated, you see an in-browser shell, where you can run commands inside your container.
Note
Any changes you make outside the /home directory are stored in the container itself and don't persist beyond an app restart.
To open a remote SSH session from your local machine, see Open SSH session from remote shell.
Troubleshooting tools
The built-in Java images are based on the Alpine Linux operating system. Use the apk package manager to install any troubleshooting tools or commands.
Flight Recorder
All Java runtimes on App Service using the Azul JVMs come with the Zulu Flight Recorder. You can use this to record JVM, system, and application events and troubleshoot problems in your Java applications.
Timed Recording
To take a timed recording you will need the PID (Process ID) of the Java application. To find the PID, open a browser to your web app's SCM site at https://
Next, open the Debug Console in the top toolbar of the SCM site and run the following command. Replace <pid> with the process ID you copied earlier. This command will start a 30 second profiler recording of your Java application and generate a file named timed_recording_example.jfr in the D:home directory.
SSH into your App Service and run the jcmd command to see a list of all the Java processes running. In addition to jcmd itself, you should see your Java application running with a process ID number (pid).
Execute the command below to start a 30-second recording of the JVM. This will profile the JVM and create a JFR file named jfr_example.jfr in the home directory. (Replace 116 with the pid of your Java app.)
During the 30 second interval, you can validate the recording is taking place by running jcmd 116 JFR.check. This will show all recordings for the given Java process.
Continuous Recording
You can use Zulu Flight Recorder to continuously profile your Java application with minimal impact on runtime performance (source). To do so, run the following Azure CLI command to create an App Setting named JAVA_OPTS with the necessary configuration. The contents of the JAVA_OPTS App Setting are passed to the java command when your app is started.
Once the recording has started, you can dump the current recording data at any time using the JFR.dump command.
Analyze .jfr files
Use FTPS to download your JFR file to your local machine. To analyze the JFR file, download and install Zulu Mission Control. For instructions on Zulu Mission Control, see the Azul documentation and the installation instructions.
App logging
Enable application logging through the Azure portal or Azure CLI to configure App Service to write your application's standard console output and standard console error streams to the local filesystem or Azure Blob Storage. Logging to the local App Service filesystem instance is disabled 12 hours after it is configured. If you need longer retention, configure the application to write output to a Blob storage container. Your Java and Tomcat app logs can be found in the /home/LogFiles/Application/ directory.
Enable application logging through the Azure portal or Azure CLI to configure App Service to write your application's standard console output and standard console error streams to the local filesystem or Azure Blob Storage. If you need longer retention, configure the application to write output to a Blob storage container. Your Java and Tomcat app logs can be found in the /home/LogFiles/Application/ directory.
Azure Blob Storage logging for Linux based App Services can only be configured using Azure Monitor (preview)
If your application uses Logback or Log4j for tracing, you can forward these traces for review into Azure Application Insights using the logging framework configuration instructions in Explore Java trace logs in Application Insights.
Customization and tuning
Azure App Service for Linux supports out of the box tuning and customization through the Azure portal and CLI. Review the following articles for non-Java-specific web app configuration:
Set Java runtime options
To set allocated memory or other JVM runtime options, create an app setting named JAVA_OPTS with the options. App Service passes this setting as an environment variable to the Java runtime when it starts.
In the Azure portal, under Application Settings for the web app, create a new app setting named JAVA_OPTS that includes the additional settings, such as -Xms512m -Xmx1204m.
To configure the app setting from the Maven plugin, add setting/value tags in the Azure plugin section. The following example sets a specific minimum and maximum Java heap size:
Developers running a single application with one deployment slot in their App Service plan can use the following options:
- B1 and S1 instances:
-Xms1024m -Xmx1024m - B2 and S2 instances:
-Xms3072m -Xmx3072m - B3 and S3 instances:
-Xms6144m -Xmx6144m
When tuning application heap settings, review your App Service plan details and take into account multiple applications and deployment slot needs to find the optimal allocation of memory.
Turn on web sockets
Turn on support for web sockets in the Azure portal in the Application settings for the application. You'll need to restart the application for the setting to take effect.
Turn on web socket support using the Azure CLI with the following command:
Then restart your application:
Set default character encoding
In the Azure portal, under Application Settings for the web app, create a new app setting named JAVA_OPTS with value -Dfile.encoding=UTF-8.
Alternatively, you can configure the app setting using the App Service Maven plugin. Add the setting name and value tags in the plugin configuration:
Java_opts Environment Variable
Pre-Compile JSP files
To improve performance of Tomcat applications, you can compile your JSP files before deploying to App Service. You can use the Maven plugin provided by Apache Sling, or using this Ant build file.
Secure applications
Java applications running in App Service have the same set of security best practices as other applications.
Authenticate users (Easy Auth)
Set up app authentication in the Azure portal with the Authentication and Authorization option. From there, you can enable authentication using Azure Active Directory or social logins like Facebook, Google, or GitHub. Azure portal configuration only works when configuring a single authentication provider. For more information, see Configure your App Service app to use Azure Active Directory login and the related articles for other identity providers. If you need to enable multiple sign-in providers, follow the instructions in the customize App Service authentication article.
Java SE
Spring Boot developers can use the Azure Active Directory Spring Boot starter to secure applications using familiar Spring Security annotations and APIs. Be sure to increase the maximum header size in your application.properties file. We suggest a value of 16384.
Tomcat
Your Tomcat application can access the user's claims directly from the servlet by casting the Principal object to a Map object. The Map object will map each claim type to a collection of the claims for that type. In the code below, request is an instance of HttpServletRequest.
Now you can inspect the Map object for any specific claim. For example, the following code snippet iterates through all the claim types and prints the contents of each collection.
To sign users out, use the /.auth/ext/logout path. To perform other actions, please see the documentation on App Service Authentication and Authorization usage. There is also official documentation on the Tomcat HttpServletRequest interface and its methods. The following servlet methods are also hydrated based on your App Service configuration:
To disable this feature, create an Application Setting named WEBSITE_AUTH_SKIP_PRINCIPAL with a value of 1. To disable all servlet filters added by App Service, create a setting named WEBSITE_SKIP_FILTERS with a value of 1.
Configure TLS/SSL
Follow the instructions in the Secure a custom DNS name with an SSL binding in Azure App Service to upload an existing SSL certificate and bind it to your application's domain name. By default your application will still allow HTTP connections-follow the specific steps in the tutorial to enforce SSL and TLS.
Use KeyVault References
Azure KeyVault provides centralized secret management with access policies and audit history. You can store secrets (such as passwords or connection strings) in KeyVault and access these secrets in your application through environment variables.
First, follow the instructions for granting your app access to Key Vault and making a KeyVault reference to your secret in an Application Setting. You can validate that the reference resolves to the secret by printing the environment variable while remotely accessing the App Service terminal.
To inject these secrets in your Spring or Tomcat configuration file, use environment variable injection syntax (${MY_ENV_VAR}). For Spring configuration files, please see this documentation on externalized configurations.
Use the Java Key Store
By default, any public or private certificates uploaded to App Service Linux will be loaded into the respective Java Key Stores as the container starts. After uploading your certificate, you will need to restart your App Service for it to be loaded into the Java Key Store. Public certificates are loaded into the Key Store at $JAVA_HOME/jre/lib/security/cacerts, and private certificates are stored in $JAVA_HOME/lib/security/client.jks.
Additional configuration may be necessary for encrypting your JDBC connection with certificates in the Java Key Store. Please refer to the documentation for your chosen JDBC driver.
Initialize the Java Key Store
To initialize the import java.security.KeyStore object, load the keystore file with the password. The default password for both key stores is 'changeit'.
Eclipse Environment Variables Java
Manually load the key store
You can load certificates manually to the key store. Create an app setting, SKIP_JAVA_KEYSTORE_LOAD, with a value of 1 to disable App Service from loading the certificates into the key store automatically. All public certificates uploaded to App Service via the Azure portal are stored under /var/ssl/certs/. Private certificates are stored under /var/ssl/private/.
You can interact or debug the Java Key Tool by opening an SSH connection to your App Service and running the command keytool. See the Key Tool documentation for a list of commands. For more information on the KeyStore API, please refer to the official documentation.
Configure APM platforms
This section shows how to connect Java applications deployed on Azure App Service on Linux with the NewRelic and AppDynamics application performance monitoring (APM) platforms.
Configure New Relic
Create a NewRelic account at NewRelic.com
Download the Java agent from NewRelic, it will have a file name similar to newrelic-java-x.x.x.zip.
Copy your license key, you'll need it to configure the agent later.
SSH into your App Service instance and create a new directory /home/site/wwwroot/apm.
Upload the unpacked NewRelic Java agent files into a directory under /home/site/wwwroot/apm. The files for your agent should be in /home/site/wwwroot/apm/newrelic.
Modify the YAML file at /home/site/wwwroot/apm/newrelic/newrelic.yml and replace the placeholder license value with your own license key.
In the Azure portal, browse to your application in App Service and create a new Application Setting.
- For Java SE apps, create an environment variable named
JAVA_OPTSwith the value-javaagent:/home/site/wwwroot/apm/newrelic/newrelic.jar. - For Tomcat, create an environment variable named
CATALINA_OPTSwith the value-javaagent:/home/site/wwwroot/apm/newrelic/newrelic.jar.
- For Java SE apps, create an environment variable named
Create a NewRelic account at NewRelic.com
Download the Java agent from NewRelic, it will have a file name similar to newrelic-java-x.x.x.zip.
Copy your license key, you'll need it to configure the agent later.
SSH into your App Service instance and create a new directory /home/site/wwwroot/apm.
Upload the unpacked NewRelic Java agent files into a directory under /home/site/wwwroot/apm. The files for your agent should be in /home/site/wwwroot/apm/newrelic.
Modify the YAML file at /home/site/wwwroot/apm/newrelic/newrelic.yml and replace the placeholder license value with your own license key.
In the Azure portal, browse to your application in App Service and create a new Application Setting.
- For Java SE apps, create an environment variable named
JAVA_OPTSwith the value-javaagent:/home/site/wwwroot/apm/newrelic/newrelic.jar. - For Tomcat, create an environment variable named
CATALINA_OPTSwith the value-javaagent:/home/site/wwwroot/apm/newrelic/newrelic.jar.
- For Java SE apps, create an environment variable named
If you already have an environment variable for JAVA_OPTS or CATALINA_OPTS, append the -javaagent:/.. option to the end of the current value.
Configure AppDynamics
Create an AppDynamics account at AppDynamics.com
Download the Java agent from the AppDynamics website, the file name will be similar to AppServerAgent-x.x.x.xxxxx.zip
Use the Kudu console to create a new directory /home/site/wwwroot/apm.
Upload the Java agent files into a directory under /home/site/wwwroot/apm. The files for your agent should be in /home/site/wwwroot/apm/appdynamics.
In the Azure portal, browse to your application in App Service and create a new Application Setting.
- For Java SE apps, create an environment variable named
JAVA_OPTSwith the value-javaagent:/home/site/wwwroot/apm/appdynamics/javaagent.jar -Dappdynamics.agent.applicationName=<app-name>where<app-name>is your App Service name. - For Tomcat apps, create an environment variable named
CATALINA_OPTSwith the value-javaagent:/home/site/wwwroot/apm/appdynamics/javaagent.jar -Dappdynamics.agent.applicationName=<app-name>where<app-name>is your App Service name.
- For Java SE apps, create an environment variable named
Create an AppDynamics account at AppDynamics.com
Download the Java agent from the AppDynamics website, the file name will be similar to AppServerAgent-x.x.x.xxxxx.zip
SSH into your App Service instance and create a new directory /home/site/wwwroot/apm.
Upload the Java agent files into a directory under /home/site/wwwroot/apm. The files for your agent should be in /home/site/wwwroot/apm/appdynamics.
In the Azure portal, browse to your application in App Service and create a new Application Setting.
- For Java SE apps, create an environment variable named
JAVA_OPTSwith the value-javaagent:/home/site/wwwroot/apm/appdynamics/javaagent.jar -Dappdynamics.agent.applicationName=<app-name>where<app-name>is your App Service name. - For Tomcat apps, create an environment variable named
CATALINA_OPTSwith the value-javaagent:/home/site/wwwroot/apm/appdynamics/javaagent.jar -Dappdynamics.agent.applicationName=<app-name>where<app-name>is your App Service name.
- For Java SE apps, create an environment variable named
Note
If you already have an environment variable for JAVA_OPTS or CATALINA_OPTS, append the -javaagent:/.. option to the end of the current value.
Configure data sources
Java SE
To connect to data sources in Spring Boot applications, we suggest creating connection strings and injecting them into your application.properties file.
In the 'Configuration' section of the App Service page, set a name for the string, paste your JDBC connection string into the value field, and set the type to 'Custom'. You can optionally set this connection string as slot setting.
This connection string is accessible to our application as an environment variable named
CUSTOMCONNSTR_<your-string-name>. For example, the connection string we created above will be namedCUSTOMCONNSTR_exampledb.In your application.properties file, reference this connection string with the environment variable name. For our example, we would use the following.
Please see the Spring Boot documentation on data access and externalized configurations for more information on this topic.
Tomcat
These instructions apply to all database connections. You will need to fill placeholders with your chosen database's driver class name and JAR file. Provided is a table with class names and driver downloads for common databases.
| Database | Driver Class Name | JDBC Driver |
|---|---|---|
| PostgreSQL | org.postgresql.Driver | Download |
| MySQL | com.mysql.jdbc.Driver | Download (Select 'Platform Independent') |
| SQL Server | com.microsoft.sqlserver.jdbc.SQLServerDriver | Download |
To configure Tomcat to use Java Database Connectivity (JDBC) or the Java Persistence API (JPA), first customize the CATALINA_OPTS environment variable that is read in by Tomcat at start-up. Set these values through an app setting in the App Service Maven plugin:
Or set the environment variables in the Configuration > Application Settings page in the Azure portal.
Java Home Environment Variables
Next, determine if the data source should be available to one application or to all applications running on the Tomcat servlet.
Application-level data sources
Create a context.xml file in the META-INF/ directory of your project. Create the META-INF/ directory if it does not exist.
In context.xml, add a
Contextelement to link the data source to a JNDI address. Replace thedriverClassNameplaceholder with your driver's class name from the table above.Update your application's web.xml to use the data source in your application.
Finalize configuration
Finally, we will place the driver JARs in the Tomcat classpath and restart your App Service. Ensure that the JDBC driver files are available to the Tomcat classloader by placing them in the /home/tomcat/lib directory. (Create this directory if it does not already exist.) To upload these files to your App Service instance, perform the following steps:
In the Cloud Shell, install the webapp extension:
Run the following CLI command to create an SSH tunnel from your local system to App Service:
Connect to the local tunneling port with your SFTP client and upload the files to the /home/tomcat/lib folder.
Alternatively, you can use an FTP client to upload the JDBC driver. Follow these instructions for getting your FTP credentials.
Tomcat
These instructions apply to all database connections. You will need to fill placeholders with your chosen database's driver class name and JAR file. Provided is a table with class names and driver downloads for common databases.
| Database | Driver Class Name | JDBC Driver |
|---|---|---|
| PostgreSQL | org.postgresql.Driver | Download |
| MySQL | com.mysql.jdbc.Driver | Download (Select 'Platform Independent') |
| SQL Server | com.microsoft.sqlserver.jdbc.SQLServerDriver | Download |
To configure Tomcat to use Java Database Connectivity (JDBC) or the Java Persistence API (JPA), first customize the CATALINA_OPTS environment variable that is read in by Tomcat at start-up. Set these values through an app setting in the App Service Maven plugin:
Or set the environment variables in the Configuration > Application Settings page in the Azure portal.
Next, determine if the data source should be available to one application or to all applications running on the Tomcat servlet.
Application-level data sources
Create a context.xml file in the META-INF/ directory of your project. Create the META-INF/ directory if it does not exist.
In context.xml, add a
Contextelement to link the data source to a JNDI address. Replace thedriverClassNameplaceholder with your driver's class name from the table above.Update your application's web.xml to use the data source in your application.
Shared server-level resources
Adding a shared, server-level data source will require you to edit Tomcat's server.xml. First, upload a startup script and set the path to the script in Configuration > Startup Command. You can upload the startup script using FTP.
Your startup script will make an xsl transform to the server.xml file and output the resulting xml file to /usr/local/tomcat/conf/server.xml. The startup script should install libxslt via apk. Your xsl file and startup script can be uploaded via FTP. Below is an example startup script.
An example xsl file is provided below. The example xsl file adds a new connector node to the Tomcat server.xml.
Finalize configuration
Finally, place the driver JARs in the Tomcat classpath and restart your App Service.
Ensure that the JDBC driver files are available to the Tomcat classloader by placing them in the /home/tomcat/lib directory. (Create this directory if it does not already exist.) To upload these files to your App Service instance, perform the following steps:
- In the Cloud Shell, install the webapp extension:
- Run the following CLI command to create an SSH tunnel from your local system to App Service:
- Connect to the local tunneling port with your SFTP client and upload the files to the /home/tomcat/lib folder.
Alternatively, you can use an FTP client to upload the JDBC driver. Follow these instructions for getting your FTP credentials.
If you created a server-level data source, restart the App Service Linux application. Tomcat will reset
CATALINA_BASEto/home/tomcatand use the updated configuration.
JBoss EAP
There are three core steps when registering a data source with JBoss EAP: uploading the JDBC driver, adding the JDBC driver as a module, and registering the module. App Service is a stateless hosting service, so the configuration commands for adding and registering the data source module must be scripted and applied as the container starts.
Obtain your database's JDBC driver.
Create an XML module definition file for the JDBC driver. The example shown below is a module definition for PostgreSQL.
Put your JBoss CLI commands into a file named
jboss-cli-commands.cli. The JBoss commands must add the module and register it as a data source. The example below shows the JBoss CLI commands for PostgreSQL.Create a startup script,
startup_script.shthat calls the JBoss CLI commands. The example below shows how to call yourjboss-cli-commands.cli. Later you will configre App Service to run this script when the container starts.Using an FTP client of your choice, upload your JDBC driver,
jboss-cli-commands.cli,startup_script.sh, and the module definition to/site/deployments/tools/.Configure your site to run
startup_script.shwhen the container starts. In the Azure Portal, navigate to Configuration > General Settings > Startup Command. Set the startup command field to/home/site/deployments/tools/startup_script.sh. Save your changes.
To confirm that the datasource was added to the JBoss server, SSH into your webapp and run $JBOSS_HOME/bin/jboss-cli.sh --connect. Once you are connected to JBoss run the /subsystem=datasources:read-resource to print a list of the data sources.
robots933456 in logs
You may see the following message in the container logs:
You can safely ignore this message. /robots933456.txt is a dummy URL path that App Service uses to check if the container is capable of serving requests. A 404 response simply indicates that the path doesn't exist, but it lets App Service know that the container is healthy and ready to respond to requests.
Choosing a Java runtime version
App Service allows users to choose the major version of the JVM, such as Java 8 or Java 11, as well as the minor version, such as 1.8.0_232 or 11.0.5. You can also choose to have the minor version automatically updated as new minor versions become available. In most cases, production sites should use pinned minor JVM versions. This will prevent unnanticipated outages during a minor version auto-update.
If you choose to pin the minor version, you will need to periodically update the JVM minor version on the site. To ensure that your application runs on the newer minor version, create a staging slot and increment the minor version on the staging site. Once you have confirmed the application runs correctly on the new minor version, you can swap the staging and production slots.
JBoss EAP hardware options
JBoss EAP is only available on the Premium and Isolated hardware options. Customers that created a JBoss EAP site on a Free, Shared, Basic, or Standard tier during the public preview should scale up to Premium or Isolated hardware tier to avoid unexpected behavior.
Java runtime statement of support
JDK versions and maintenance
Azure's supported Java Development Kit (JDK) is Zulu provided through Azul Systems. Azul Zulu Enterprise builds of OpenJDK are a no-cost, multi-platform, production-ready distribution of the OpenJDK for Azure and Azure Stack backed by Microsoft and Azul Systems. They contain all the components for building and running Java SE applications. You can install the JDK from Java JDK Installation.
Major version updates will be provided through new runtime options in Azure App Service. Customers update to these newer versions of Java by configuring their App Service deployment and are responsible for testing and ensuring the major update meets their needs.
Supported JDKs are automatically patched on a quarterly basis in January, April, July, and October of each year. For more information on Java on Azure, please see this support document.
Security updates
Java Read Environment Variable
Patches and fixes for major security vulnerabilities will be released as soon as they become available from Azul Systems. A 'major' vulnerability is defined by a base score of 9.0 or higher on the NIST Common Vulnerability Scoring System, version 2.
Tomcat 8.0 has reached End of Life (EOL) as of September 30, 2018. While the runtime is still available on Azure App Service, Azure will not apply security updates to Tomcat 8.0. If possible, migrate your applications to Tomcat 8.5 or 9.0. Both Tomcat 8.5 and 9.0 are available on Azure App Service. See the official Tomcat site for more information.
Deprecation and retirement
If a supported Java runtime will be retired, Azure developers using the affected runtime will be given a deprecation notice at least six months before the runtime is retired.
Local development
Developers can download the Production Edition of Azul Zulu Enterprise JDK for local development from Azul's download site.
Development support
Product support for the Azure-supported Azul Zulu JDK is available through Microsoft when developing for Azure or Azure Stack with a qualified Azure support plan.
Next steps
Visit the Azure for Java Developers center to find Azure quickstarts, tutorials, and Java reference documentation.
General questions about using App Service for Linux that aren't specific to the Java development are answered in the App Service Linux FAQ.
Java is a very popular programming language which provides a different component in order to run, develop Java applications. JRE or Java Runtime Environment is used to run Java application. JDK or Java Development Kit is used to develop Java applications. In this tutorial, we will learn how to set up Java, JRE, and JDK operating system path variables in order to work properly.
Before starting the configuration we have to locate the JRE or JDK path. JRE or JDK generally installed on the Program Files or Program Files(x86) directory under the Java directory like below.
and under the Java directory the JDK is residing.
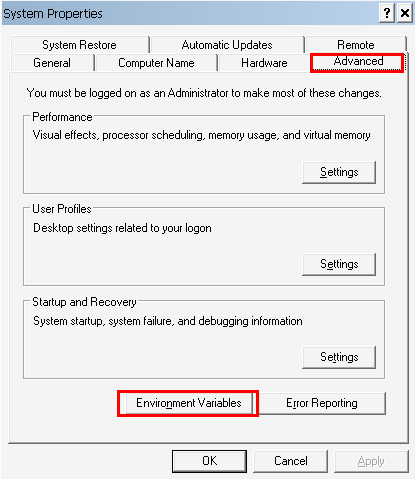
Now we have learned the path of the Java, JRE or JDK installation. We can set this path as Java HOME_PATH environment variable. We will open the computer properties with by running sysdm.cpl in the Run menu like below. We can also open it from the File Explorer -> Computer -> Right Click.
In the system properties, we will navigate to the Advanced tab which provides the Environment Variables button like below.
Below we can see the environment variables menu where we will create the JAVA_HOME system variable and set the path accordingly. We click to the New in order to create a new system variable.
Here we will set the Variable Name as JAVA_HOME and the Variable Value the path or Java, JRE or JDK which is C:Program FilesJavajdk-12 in this example. Then we will click OK.
If we want to run java.exe or similar executables provided by JRE or JDK we have to add the path of Java in the Path variable like below. We select the system variable named Path and click to the Edit.
Here we click to New which will add a new line to the existing values.
Here we will set the bin folder path which is C:Program FilesJavajdk-12bin in this example.
Java_opts Environment Variable Vs
Then we will click OK and OK in the environment variables screen which will save and activated new path configuration.
We can check the new path configuration simply opening a new command line interface MS-DOS. Then just type java -version which will execute java.exe with the -version option. We can see the current java binary version by running it.
